Operational Resilience
Get to the root of operational risk - People and Process
Resilience Starts with Insight
Prepare for disruption, sustain critical services, and recover with confidence. This assessment offers a clear, actionable view of your operational resilience by evaluating cybersecurity and ITSM maturity. Discover how our AI-powered reports turn your assessment data into strategic, actionable insights.
NIST CSF 2.0 Meets ITSM
Navvia's Cybersecurity Risk Assessment is an innovative solution that integrates the key security outcomes from NIST CSF 2.0 with your IT Service Management (ITSM) processes. This practical solution helps you focus on the relevant security practices and the necessary processes to maintain and improve your security posture.

Benefits
Why Choose Our Operational Resilience Assessment?

Our approach bridges cybersecurity and IT Service Management (ITSM) to give leaders a unified view of operational resilience. NIST CSF defines critical security outcomes; ITSM ensures the right processes are in place to sustain them. Together, they offer a pragmatic framework to reduce risk, minimize disruption, and support long-term continuity.
For example, while cybersecurity may highlight third-party risk, ITSM ensures supplier processes are in place to manage that risk at scale. This integrated view empowers leadership to make informed decisions that align with organizational priorities.
Other benefits include

Aligns with Resilience and Governance Frameworks
Aligns your organization with leading standards such as NIST CSF, ITSM, and resilience principles. Strengthens governance, improves accountability, and supports a culture of risk-aware service delivery.

Identifies Systemic Gaps for Targeted Investment
Uses structured assessments to reveal gaps in security controls and IT processes. Enables smart prioritization of resources to improve continuity, availability, and risk posture.

Supports Continuous Operational Maturity
Establishes a repeatable model to track improvement across cybersecurity and ITSM. Helps you adapt to evolving threats, improve service reliability, and demonstrate resilience over time.

Strengthens Strategic Confidence
Offers leadership-ready insights to validate risk investments, enhance business continuity planning, and align resilience efforts with strategic goals.

Enhances Compliance and Risk Assurance
Simplifies audit readiness by aligning security and ITSM processes with regulatory requirements. Improves control design and reduces compliance gaps.
Improves Organizational Readiness
Promotes awareness of risks and dependencies across departments. Equips teams to respond proactively, reducing the impact of service disruptions or cyber incidents.
How it works?
We provide a set of questionnaires that assess your organization’s operational resilience posture. Six assessments align with NIST CSF functions — Govern, Identify, Protect, Detect, Respond, and Recover — focusing on cybersecurity outcomes. Thirteen additional assessments evaluate ITSM processes with a resilience lens, ensuring the right operational capabilities are in place to support those outcomes.
This dual framework allows leaders to:
- Measure how security controls are supported by process maturity
- Understand where resilience gaps exist across services and suppliers
- Prioritize improvements that reduce operational and cyber risk
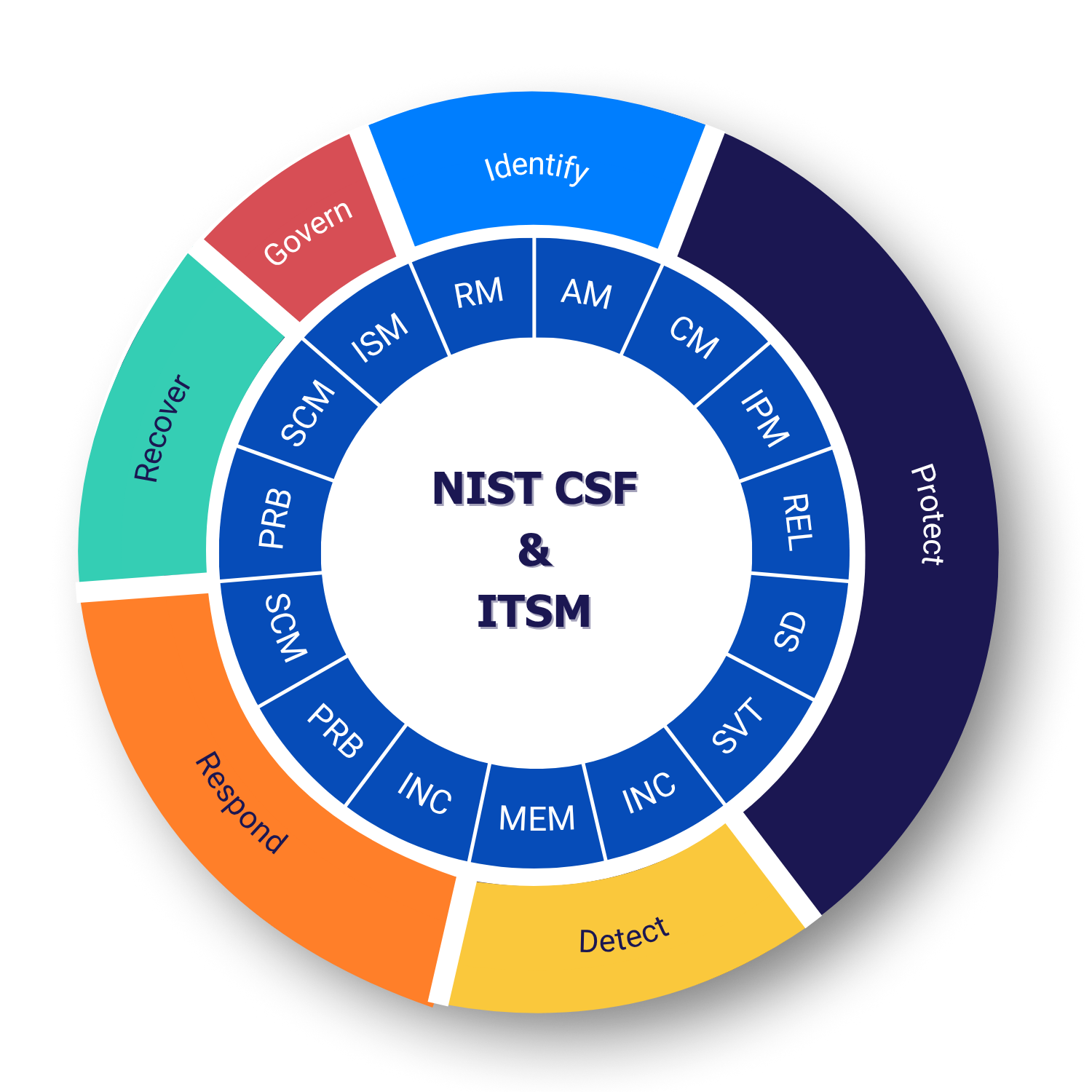
ITSM processes covered:
Risk Management
 Identifies, assesses, and mitigates security risks to protect systems and data. Ensures proactive threat management by applying security controls and monitoring vulnerabilities. Helps prevent incidents and minimize potential damage.
Identifies, assesses, and mitigates security risks to protect systems and data. Ensures proactive threat management by applying security controls and monitoring vulnerabilities. Helps prevent incidents and minimize potential damage.
IT Asset Management
 Tracks and manages IT assets to ensure they are secure, updated, and properly controlled. Reduces unauthorized access, ensures timely patching, and prevents security gaps. Supports compliance and strengthens overall IT security.
Tracks and manages IT assets to ensure they are secure, updated, and properly controlled. Reduces unauthorized access, ensures timely patching, and prevents security gaps. Supports compliance and strengthens overall IT security.
Software Development & Management
 Integrates security best practices into software design, testing, and updates. Reduces vulnerabilities by enforcing secure coding, regular testing, and controlled updates. Helps prevent exploitation of software flaws and unauthorized access.
Integrates security best practices into software design, testing, and updates. Reduces vulnerabilities by enforcing secure coding, regular testing, and controlled updates. Helps prevent exploitation of software flaws and unauthorized access.
Release Management
 Ensures secure and controlled deployment of software and system changes. Reduces risks by following structured testing, approval, and rollback procedures. Prevents misconfigurations, security gaps, and service disruptions.
Ensures secure and controlled deployment of software and system changes. Reduces risks by following structured testing, approval, and rollback procedures. Prevents misconfigurations, security gaps, and service disruptions.
Validation & Testing
 Confirms that security controls are in place and functioning before deployment. Uses security testing, vulnerability scans, and penetration testing to detect and address weaknesses. Ensures systems are resilient against threats before release.
Confirms that security controls are in place and functioning before deployment. Uses security testing, vulnerability scans, and penetration testing to detect and address weaknesses. Ensures systems are resilient against threats before release.
Infrastructure Management
 Maintains secure IT environments by applying updates, managing configurations, and enforcing security policies. Reduces exposure to cyber threats by ensuring networks, servers, and systems are properly protected. Supports business continuity by maintaining stability and resilience.
Maintains secure IT environments by applying updates, managing configurations, and enforcing security policies. Reduces exposure to cyber threats by ensuring networks, servers, and systems are properly protected. Supports business continuity by maintaining stability and resilience.
Monitoring and Event Management
 Continuously tracks system activity and detects suspicious behavior to identify potential threats early. Uses security monitoring tools, alerts, and automated responses to minimize risk. Helps prevent and respond to security incidents efficiently.
Continuously tracks system activity and detects suspicious behavior to identify potential threats early. Uses security monitoring tools, alerts, and automated responses to minimize risk. Helps prevent and respond to security incidents efficiently.
Incident Management
 Ensures quick response and recovery from security breaches and IT disruptions. Minimizes damage by detecting, containing, and resolving incidents effectively. Strengthens security by analyzing root causes and implementing improvements.
Ensures quick response and recovery from security breaches and IT disruptions. Minimizes damage by detecting, containing, and resolving incidents effectively. Strengthens security by analyzing root causes and implementing improvements.
Problem Management
 Identifies and resolves the root causes of security and IT issues to prevent future incidents. By addressing vulnerabilities and recurring threats, it strengthens defenses, reduces downtime, and improves cybersecurity resilience.
Identifies and resolves the root causes of security and IT issues to prevent future incidents. By addressing vulnerabilities and recurring threats, it strengthens defenses, reduces downtime, and improves cybersecurity resilience.
Service Continuity Management
 Maintains IT service availability during security incidents or system failures. Implements recovery strategies, backups, and failover mechanisms to reduce downtime. Ensures businesses can continue operations securely and efficiently.
Maintains IT service availability during security incidents or system failures. Implements recovery strategies, backups, and failover mechanisms to reduce downtime. Ensures businesses can continue operations securely and efficiently.
Information Security Management
 Defines and enforces security policies, controls, and compliance requirements to protect data and systems. Manages risks, enforces access controls, and ensures security best practices are followed. Strengthens overall cybersecurity posture and regulatory compliance.
Defines and enforces security policies, controls, and compliance requirements to protect data and systems. Manages risks, enforces access controls, and ensures security best practices are followed. Strengthens overall cybersecurity posture and regulatory compliance.
Supplier Management
 Ensures vendors and third-party providers meet security requirements to prevent supply chain risks. Evaluates and monitors external partners to reduce vulnerabilities and unauthorized access. Strengthens security by enforcing contractual security obligations and risk assessments.
Ensures vendors and third-party providers meet security requirements to prevent supply chain risks. Evaluates and monitors external partners to reduce vulnerabilities and unauthorized access. Strengthens security by enforcing contractual security obligations and risk assessments.
Change Management
 Ensures changes to IT systems and services are evaluated, authorized, and implemented with minimal disruption. Reduces operational risk by enforcing structured approval workflows, risk assessments, and rollback plans. Strengthens resilience by maintaining service stability and ensuring critical changes support business continuity and security objectives.
Ensures changes to IT systems and services are evaluated, authorized, and implemented with minimal disruption. Reduces operational risk by enforcing structured approval workflows, risk assessments, and rollback plans. Strengthens resilience by maintaining service stability and ensuring critical changes support business continuity and security objectives.

Insights at a glance
See your assessment results come to life. Navvia’s AI reports highlight strengths, gaps, and trends, so you can act on insights faster.
Detailed analysis
Dive into the data behind each assessment. AI-driven insights identify patterns, anomalies, and opportunities for improvement.
Executive summaries
Get concise overviews of your organization’s operational resilience. Understand key findings and priorities at a glance.
Actionable recommendations
Receive prioritized steps to strengthen resilience, with clear guidance on what to do next and why.
Use our Survey tool to target the right internal or external stakeholders and collect assessment data. Generate reports to measure your overall capability and identify gaps. AI-powered reports go further, uncovering hidden patterns, highlighting trends, and providing prioritized recommendations to guide your next steps.

Broad Reach & Scalability
Easily distribute assessments to an unlimited number of respondents, ensuring broad participation across teams, departments, and external stakeholders. This allows for comprehensive data collection without restrictions, helping organizations gain valuable insights from a diverse audience.

Smart Segmentation & Analytics
Organize responses by specific groups such as management, subject matter experts (SMEs), or general users to gain more targeted insights. Segmentation makes it easier to analyze trends, compare responses across different roles, and tailor security improvements to specific areas of the organization.

Secure Evidence Collection
Allow respondents to upload supporting documents, screenshots, or links to validate their answers. This feature ensures accurate reporting and compliance by maintaining a centralized repository of evidence, making audits and follow-ups more efficient.
Automated Survey Tracking & Reminders
Monitor response rates in real time and send automated reminders to participants who have not yet completed the assessment. This ensures higher completion rates while reducing the need for manual follow-ups, saving time and effort.

Comprehensive Reporting & Insights
Generate detailed reports to visualize trends, identify security gaps, and track progress over time. Reports can be exported in multiple formats, making it easy to share findings with leadership, compliance teams, or external auditors.
What Our Clients Are Saying
Here is what one of our customers, an international manufacturer of pharma, medical, and consumer products, has to say:
Want to Learn More
Reach out to us today, and a member of our team will be in touch with you shortly
Cyber Security Articles
Explore our IT security article for essential strategies to protect your systems, data, and networks from evolving cyber threats. Stay informed and secure with expert tips to safeguard your digital infrastructure.

The Illusion of Security:
Why Technology isn't Enough
Imagine yourself as a world-class spy tasked with infiltrating a top-secret facility. This site boasts formidable defenses, complete with high-tech surveillance cameras and state-of-the-art motion, temperature, and pressure sensors. At first glance, it sounds impenetrable. Or does it?

How to Implement IT Security Management: The Ultimate Guide
IT security management is a top priority for executives, especially in today’s digital era. As cyber threats grow, strong security is vital for maintaining trust and compliance. This guide offers key concepts and practical steps to improve security, with valuable insights for both newcomers and experts.

The Human Factors in Cyber Security: Strategies for Effective Defense


The Fundamentals of NIST CSF 2.0: What it is and Why Its Important
Security risks are around every corner. Organizations now, more than ever, require a structured approach to identify, protect, detect, resolve, and recover from threats and vulnerabilities. The NIST Cybersecurity Framework offers this structure with flexibility and effectiveness!

The Truth Behind a Cyber Breach: How Human Error and Process Failures Lead to Security Incidents
Hollywood would have you believe that the "black hats" breach our systems through their technical prowess and mad cyber skills. Truth is, it's human error and broken processes that let them through the door.

NIST CSF 2.0 & ITSM: A Powerful Approach to Security Assessments
Cyber threats are evolving, and traditional “technology-driven” security measures are not enough. In this webinar, we explore how integrating the NIST Cybersecurity Framework (CSF) and IT Service Management (ITSM) can create a stronger, process-driven defense against cyber threats. 

5 Ways IT Service Management - ITSM Enhances IT Security

What Is an Information Security Management System and Why It Matters?
An Information Security Management System (ISMS) is the foundation for your organization's IT security program. It provides best practices and guidance for all aspects of IT security, encompassing people, processes, and technology.

Boost Cyber Resilience with IT Security Assessments and ITSM Processes
A Comprehensive Guide to Conducting a Cybersecurity Risk Assessment
![]()
For over two decades, Navvia has been a leader in helping organizations assess, design, and optimize their IT Service Management (ITSM) processes.
Our extensive experience has consistently shown that virtually every ITSM process plays a foundational role in in enabling organizations to strengthen their overall security posture.
Hackers are always seeking to exploit organizational weaknesses, and with the current threat landscape, the risk of a cyber attack is a constant concern. Research indicates that the root cause of most cybersecurity breaches can often be traced back to human errors or flawed processes, such as using weak passwords, un-patched systems, mis-configurations, inadequate testing, or poorly managing user privileges. These vulnerabilities can lead to significant data breaches and reputational harm.
In response to these challenges, InfoSec teams often invest heavily in security tools. While this is beneficial, a significant disconnect frequently persists between InfoSec and IT teams responsible for managing and implementing the company’s information systems. To address this issue, we have developed the Navvia Cybersecurity Assessment to provide organizations with a systematic process for identifying potential risks and enhancing security.
Introducing the Navvia Cybersecurity Risk Assessment
To address this challenge and bridge the gap, we developed the Navvia Cybersecurity Risk Assessment. This assessment not only evaluates an organization’s cybersecurity posture but also aligns ITSM practices with cybersecurity objectives, ensuring a cohesive approach to risk management and threat mitigation
Our assessment marries two respected frameworks, the NIST Cyber Security Framework (NIST CSF) and IT Service Management (ITSM).
The NIST CSF identifies the security outcomes an organization should strive to achieve. ITSM provided the foundational processes to achieve those outcomes. You can’t achieve one without the other!
Planning your Cybersecurity Risk Assessment
An effective cybersecurity assessment begins with thorough planning. This involves defining the scope and objectives, engaging relevant stakeholders, and holding a kickoff meeting.
Scope and Objectives
Our cybersecurity risk assessment is comprehensive, covering the six NIST Cybersecurity Framework (CSF) functions: Identify, Protect, Detect, Respond, Recover, and Govern. Additionally, it incorporates the thirteen IT Service Management (ITSM) processes that directly align with these functions, facilitating the achievement of critical business objectives.
To initiate the planning process, you need to determine two essential factors:
- Which NIST CSF functions and ITSM processes you wish to assess.
- Which parts of the organization you want to cover.
The advantage of the Navvia cybersecurity risk assessment is its flexibility; you can conduct as many assessments as desired throughout your annual subscription, eliminating the need to assess everything at once.
For example, consider the NIST CSF Identify function, which encompasses Asset Management, Risk Management, and the continuous improvement of your ability to identify, prioritize, and mitigate risks. Supporting this function are the ITSM Asset Management and Risk Management processes. The next consideration is whether you will assess the Identify function across the entire organization or focus on a specific region or department.
Engaging Stakeholders
Once the scope is established, the next step is to engage various stakeholders to secure their support and buy-in for the assessment. If you are focusing your assessment on the NIST CSF Identify function, you will need to identify key management, subject matter experts, and stakeholders. Key participants may include:
- Process Owners for IT Asset and Risk Management
- Process Managers
- Asset Owners
- Risk Managers
- Risk Analysts
- Management
- Service Owners
- InfoSec Team
Reach out to their management to obtain permission to engage these resources as part of the assessment. Additionally, determine whether you will supplement the Navvia questionnaires with interviews and workshops, utilizing the questionnaires as a guide. Workshops and interviews provide opportunities to ask follow-up questions and explore topics in greater depth.
The Kickoff Meeting
The kickoff meeting is a critical step in the planning phase, setting the stage for the assessment. It is essential to include all stakeholders and their respective senior management to demonstrate organizational support. The agenda for the kickoff should cover:
- The importance of the assessment
- Goals and objectives
- Reasons for participent selection
- Roles and expectations for the participants
- Timeline of the assessment
- Benefits of the assessment
- Nest steps
Effective planning for your assessment is vital for its success. By clearly defining the scope, engaging stakeholders appropriately, and conducting a comprehensive kickoff meeting, you lay the groundwork for a successful cybersecurity risk assessment that effectively addresses your organization's needs.
Launching your Cybersecurity Risk Assessment
Launching your cybersecurity risk assessment in Navvia is straightforward. The process involves creating a project, selecting questionnaires from our library, establishing segmentation groups, mapping participants to questionnaires and groups, composing launch and follow-up emails, and ultimately tracking engagement.
Creating the Project
Begin by navigating to our survey tool to create a new cybersecurity project. When setting up the project, provide the following details:
- Project Name: A descriptive title for easy identification.
- Project Description: An overview of the assessment's purpose and scope.
- Start and End Dates: Specify the duration of the project.
Selecting the Questionnaires
Once the project is created, open it to select from our suite of six NIST CSF questionnaires and thirteen ITSM questionnaires. You have the option to use these questionnaires as they are or customize the questions to meet your specific needs, ensuring that they address your organization's sensitive information.
Creating Segmentation Groups and Participants
Establishing segmentation groups is essential for in-depth analysis. For instance, creating different groups for management, subject matter experts (SMEs), and service owners allows for comparative analysis of responses, helping to identify high-priority activities.
After creating the segmentation groups, map participants to their respective questionnaires and groups. Participants can be easily uploaded into Navvia via a file or created using Single Sign-On (SSO). Since mapping is done at the questionnaire level, you can assign one participant as a manager for one questionnaire and as an SME for another, ensuring flexibility in participant roles.
Creating the Emails and Launching the Questionnaires
Navvia enables you to craft multiple email messages, including:
- Launch Email: To initiate the assessment and inform participants.
- Reminder Emails: To encourage participation from those who haven't completed the questionnaire.
- Project Ending Emails: To thank participants and summarize the next steps.
The system automatically includes the relevant questionnaire links in these emails based on participant mapping. Once the project is launched, you can schedule emails according to the status of the questionnaires (e.g., not started or not completed).
Tracking Engagement
Navvia offers various dashboards and reports to monitor engagement at all levels, down to individual participants. Utilize these tools to manage the overall project effectively, ensuring that you stay informed of progress and can take necessary actions to optimize participation.
Analyzing the Data
Once the cybersecurity risk assessment is complete, the next critical step is analyzing the data collected. This process involves examining various reports and visualizations to glean insights that inform your organization’s security posture and drive improvement initiatives.
Types of Reports
-
Score-Based Reports: Provide a quantitative overview of the assessment results, allowing for baseline comparisons against industry standards or previous assessments.
-
Radar Charts: Segment data by domain to visualize strengths and weaknesses effectively, enabling a quick assessment of areas that require attention.
-
Bar Charts: Compare responses by role or function, helping identify discrepancies or commonalities in understanding among different groups within the organization.
-
Heat Maps: Highlight gaps in specific areas for rapid insights, showcasing where vulnerabilities are most concentrated and warrant immediate attention.
-
Response-Based Reports:
- Response Distribution: Illustrate how responses vary across the organization.
- Responses by Group: Analyze the differences in responses across various segments, such as departments or roles.
- Capture Comments: Collect qualitative feedback from participants, providing deeper context to the numerical data.
Assessing NIST Outcomes
To gain a comprehensive understanding of your organizational security framework, evaluate NIST outcomes by function to:
- Identify weaknesses and areas needing improvement.
- Analyze categories and subcategories to pinpoint specific gaps in expected outcomes, facilitating a focused approach to remediation.
NIST CSF Outcomes are based on the percentage attainment of the NIST outcomes for each function, utilizing data collected from the questionnaire responses. This approach allows organizations to identify critical areas for enhancement and prioritize actions accordingly.
Examining Corresponding Processes
Conduct an in-depth review of corresponding ITSM processes, looking to identify:
- Gaps in execution and documentation.
- Inconsistencies in process measurement.
- Opportunities for continual improvement.
Our IT Service Management (ITSM) process maturity assessment utilizes the ISO 33020 Process Maturity Model, which evaluates processes on a scale of 1 to 5. In this model, a maturity level of 1 indicates that processes are merely Performed, signifying basic execution without any formal management. Progressing through the levels, processes are assessed as follows:
- Level 2: Managed - Processes are not only performed but actively managed to ensure efficiency and effectiveness.
- Level 3: Established - Processes are established with defined standards and practices, creating consistency across the organization.
- Level 4: Predictable - At this level, processes are monitored and controlled, allowing for predictable outcomes and performance metrics.
- Level 5: Innovating - The highest maturity level reflects processes that are continuously improved and innovated upon, adapting to new challenges and opportunities for enhancement.
This structured approach enables organizations to identify their current process maturity and establish targeted strategies for advancement, ultimately leading to enhanced service delivery and operational excellence.
Reviewing Segmentation Data
Scrutinize the segmentation data to determine if gaps are concentrated in specific areas or functions. This analysis will help prioritize actions and focus on critical vulnerabilities and high-impact areas that require immediate attention to prevent data loss, monetary losses, reputational damage and other implications of a breach.
Developing Findings and Recommendations
Leverage observations, interviews, workshops, and completed questionnaires to systematically develop findings. Organize these findings to create actionable recommendations that clearly outline the next steps for enhancing your cybersecurity efforts, including necessary remediation actions.
Report Table of Contents
Your final report should provide a comprehensive overview of the assessment process and findings. A well-structured table of contents might include:
- Assessment Methodology: Outline the processes and tools used during the assessment.
- Participants: Document the key stakeholders and their roles in the assessment.
- Key Findings by Theme: Present major insights derived from the analysis.
- Recommendations: Provide tailored action steps to address identified issues.
- Including Benefits and Implications: Discuss the potential impacts of the recommended changes.
- Roadmap: Develop a strategic plan for implementation, focusing on quick wins.
- Be Realistic: Encourage a practical approach to improvements, avoiding the pitfall of taking on too much at once.
Through thorough data analysis and strategic recommendations, your organization can significantly enhance its cybersecurity posture, ensuring robust protection against evolving threats.
The Importance of a Cybersecurity Assessment
Cybersecurity has become a fundamental component of any organization’s strategy. A cybersecurity risk assessment is crucial as it allows organizations to identify risks, assess potential threats, and develop strategies to mitigate risks associated with various vulnerabilities within their IT environment.
The risk assessment process provides a structured approach to understanding cybersecurity risks and aligning them with business objectives. By performing a cybersecurity risk assessment, organizations can gain insights into their critical assets, such as sensitive information and information systems, ensuring that adequate security measures are in place.
Utilizing recognized cybersecurity risk assessment frameworks helps in establishing a consistent assessment tool that enables organizations to systematically evaluate their security posture against emerging cyber threats and insider threats. This comprehensive analysis allows security teams to prioritize risks based on their potential impact on the organization and address high-priority activities effectively.
Key Benefits
A well-executed cybersecurity assessment delivers several key benefits:
-
Mitigate Risks: By identifying risks and vulnerabilities, organizations can take proactive measures to mitigate potential threats, reducing the likelihood of incidents that could lead to reputational damage or financial losses.
-
Ensure Compliance: Maintaining compliance with regulatory requirements—such as PCI DSS and other regulations—requires a thorough understanding of associated risk. Regular assessments help organizations maintain compliance while ensuring they meet the expectations set by governing bodies like the National Institute of Standards and Technology (NIST).
-
Informed Decision-Making: A comprehensive risk assessment process enables organizations to make informed decisions regarding their security program. By conducting a data audit of their security controls and evaluating the effectiveness of their current measures, companies can prioritize actions that yield the highest return on investment in terms of security.
-
Cost-Effective Management: Through the use of cost-benefit analysis, organizations can allocate limited resources more effectively when responding to cybersecurity risks. This strategic approach aids in the identification of weak passwords, improper user privileges, and other vulnerabilities that might not otherwise be addressed.
-
Develop a Robust Cybersecurity Program: Performing a comprehensive cybersecurity assessment fosters a culture of risk management throughout the entire organization. By engaging all stakeholders, organizations can create an effective cybersecurity program that evolves to address the changing threat landscape.
-
Earlier Mitigation of Threats: Identifying vulnerabilities early enables organizations to implement remediation actions before they become security incidents, ultimately saving time and reducing recovery costs in the event of a data breach.
In summary, the importance of a cybersecurity assessment cannot be overstated. It is essential for organizations to consistently analyze and improve their security posture in the face of evolving threats. A robust assessment helps in protecting critical assets, enhancing overall security, and ensuring regulatory compliance, all of which are vital for sustainable business success.
Conclusion
Conducting a cybersecurity risk assessment is a critical step in strengthening your organization’s security posture. By carefully planning your assessment, engaging the right stakeholders, and utilizing Navvia's assessment tools, you can effectively identify and mitigate vulnerabilities within your organization.
The integration of ITSM practices with comprehensive cybersecurity frameworks like the NIST CSF enhances your organization’s ability to respond to threats and to continue improving its security processes. This proactive approach not only addresses critical areas of concern but also helps organizations set the stage to identify threats, implement protections, identify and recover more quickly from incidents, reducing costs and the associated reputational harm associated with a breach.
By following this guide, you will be well-equipped to launch a successful cybersecurity risk assessment that not only meets compliance requirements but also fortifies your organization's defences against evolving cyber threats.
For more information on how to get started with the Navvia Cybersecurity Risk Assessment, contact us today!


