Summiting Cybersecurity with the NIST CSF: Planning the Journey
Imagine setting out to summit a mountain without a map, supplies, or even knowing where the summit is. Sounds reckless, right? Yet many organizations approach cybersecurity the same way — reactive, underprepared, and hoping for the best.
This is the first in a series of seven blog posts designed to guide you through your cybersecurity journey using the NIST Cybersecurity Framework (CSF) as your map.
What You'll Learn
In this post, you'll discover how to plan your cybersecurity ascent by defining your mission, aligning stakeholders, and creating a roadmap that supports both security and operational resilience — all guided by NIST CSF 2.0.
“Every successful summit starts long before the climb — with a plan.”
Why Planning Comes First
Cyber threats can halt production, cripple systems, and erode trust in a matter of hours. A reactive approach isn’t just risky — it’s operationally dangerous. One misstep can ripple across the business, disrupting everything from customer service and supply chains to revenue operations and compliance.
While organizations invest heavily in technology, breaches still dominate headlines. Clearly, technology alone is no longer enough.
Summiting cybersecurity requires foresight, coordination, and structure. And that’s why your journey must begin with a solid plan.
NIST CSF 2.0: Your Guidebook for the Climb
The NIST Cybersecurity Framework (CSF) 2.0 is more than a checklist — it’s a structured, outcome-driven guide to building cyber and operational resilience. Like a mountaineer’s route map, it helps you chart your course and prepare for both known and unexpected hazards.
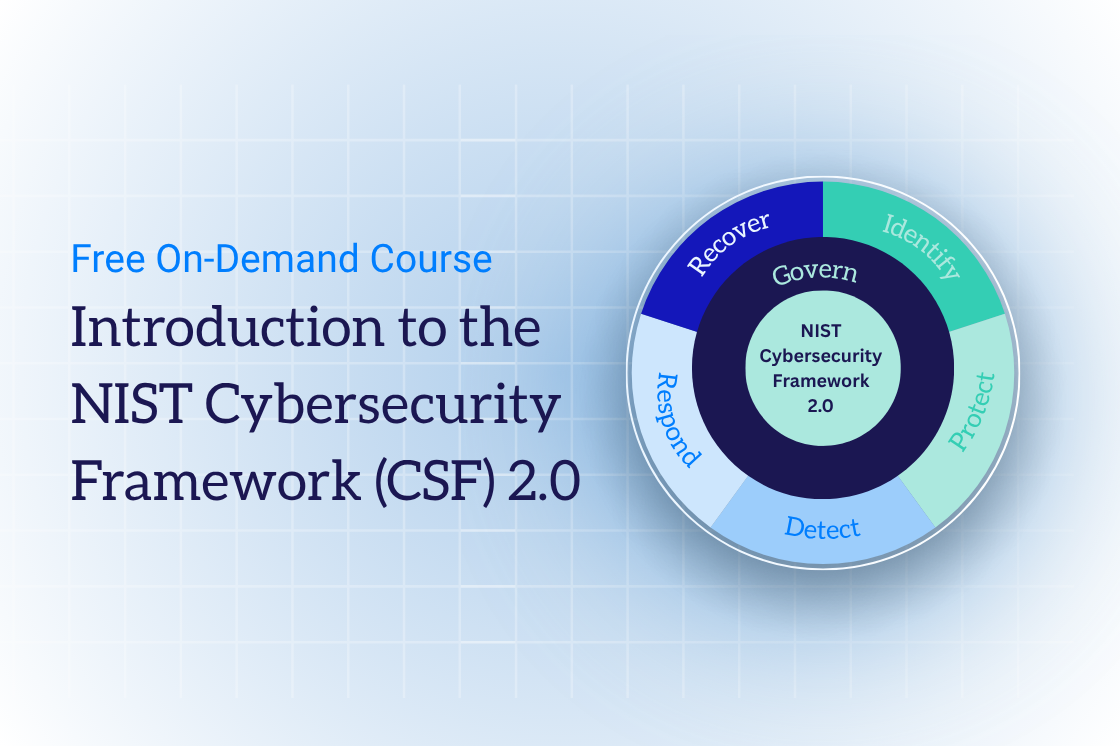
NIST CSF 2.0 introduces six core functions:
- Identify - Know your assets, risks, and dependencies
- Protect - Safeguard what matters most
- Detect - Spot and analyze potential threats early
- Respond - React effectively to incidents
- Recover - Restore affected assets and operations.
- Govern - Lead with clear policies, roles, and oversight
Each function represents a critical milestone on your path to cyber resilience. Click for an Intro to the NIST CSF 2.0
Step One: Plan the Ascent
Cybersecurity planning goes beyond technology — it’s about enabling performance under pressure.
In this phase, your organization must define its mission, align stakeholders, set priorities, and commit to a long-term roadmap.
Without a plan:
- Security efforts become fragmented and reactive.
- Operational disruptions take longer to resolve.
- Investments miss the mark.
- Accountability becomes unclear.
- Cyber initiatives remain disconnected from business operations.
With thoughtful planning, organizations gain:
- Clarity on what's important.
- Control over risks.
- Confidence in their ability to maintain Operational Resilience
From Planning to Practice
Here’s what successful cybersecurity and operational resilience planning includes:
- Define the Mission: What does resilience mean for your operations? Is it continuous uptime, data integrity, regulatory adherence, or customer trust?
- Assess the Current State: Understand your existing cybersecurity posture, key processes, and dependencies across systems and teams.
- Set Risk-Based Priorities: Focus resources on critical business functions, high-value assets, and known vulnerabilities.
- Assign Roles & Responsibilities: Ensure every function — from IT to operations to legal — knows its role before an incident occurs.
- Align with Business and Operational Goals: Security isn’t a separate track — it should enable business continuity, agility, and performance.
- Plan for Adaptability: The threat landscape changes constantly. So must your plans. Bake in flexibility, governance, and feedback loops.
Why it Matters to Executives
Executives are increasingly expected to own cyber risk — not just delegate it. Planning is how they lead from the front.
For business leaders, cybersecurity planning is risk planning. It's what ensures your business can keep moving forward — even in the face of adversity.
Effective planning helps leadership:
- Translate cyber risk into operational and financial impact.
- Align cybersecurity strategy with enterprise risk appetite.
- Support growth without introducing unacceptable exposure.
- Foster cross-functional ownership of resilience.
Don’t Start the Climb Without a Map
Cybersecurity planning might not be flashy, but it’s foundational. It ensures that when things go wrong — and they will — your organization can adapt, recover, and continue operating.
Before you take your first step, chart your route. Planning with NIST CSF 2.0 turns uncertainty into strategy — and strategy into operational resilience.
Next Up in the Series:
"Summiting Cybersecurity with the NIST CSF: Identify Risks"
Learn how to build your basecamp by understanding what you have, what’s critical, and where your operational risks lie.
About this Series: Summiting the NIST CSF is a plain-English, business-focused journey through the six core stages of cybersecurity resilience. Inspired by the climb to a summit, each step builds on the last — from Identifying Risks to Responding, Recovering, and Governing with confidence. Whether you're in the boardroom or leading operations, this guide connects cybersecurity outcomes to strategic business value.