Configuration Management Best Practices
We're pleased to provide this comprehensive guide to Configuration Management Process best practices. It's the perfect resource to help you define a new process or update an existing one!
Navvia is excited to provide the fourth best practice guide in our series of the five foundational ITSM processes every organization needs to have in place.
For each process, we provide a process description, key benefits, roles, responsibilities, a description of the significant activities, tips on process governance, and some design and implementation guidance.
Configuration Management Description
The Configuration Management process keeps precise records of an organization's Configuration Items (CI). Configuration Items (CI) refer to any item that requires management to support an IT Service. These may include services, hardware, software, locations, documentation, processes, employees, customers, etc.
Each Configuration Item (CI) is linked to several attributes. A Server CI, for instance, could have attributes that specify its asset number, location, vendor, model number, CPU type, memory, and more. The attributes vary based on the type of CI. For instance, the attributes required for a server will not be the same as those needed for a location, which may include details such as name, country, city, and address.
Information about Configuration items is kept in a Configuration Management Database (CMDB) through automated discovery tools or by manual data entry.
Capturing the relationships between each Configuration Item (CI) is crucial to Configuration Management. Understanding these relationships leads to quicker incident resolution, enhanced change management, improved release management, and effective problem management.
For instance, having knowledge of all the Configuration Items (CIs) that make up your companys "reservation system" enables you to evaluate the consequences of modifying a specific CI or determining the effects of a particular CI malfunctioning.
It's important to differentiate Configuration Management from Hardware Asset Management (HAM) or Software Asset Management (SAM). While Configuration Management collaborates closely with these processes, Asset Management primarily deals with the financial aspects of the CI, from procurement to asset retirement.
The key activities of the Configuration Managment process includes:
- Configuration Managment Planning
- Configuration Item (CI) Identification
- Configuration Control
- Verification and Audit
- Status Accounting and Reporting
Configuration Management Benefits
Configration management provides organizations with the following benefits:
- Faster Incident and problem resolution: With configuration management, organizations can quickly identify and resolve issues by having a comprehensive view of system configurations and dependencies. It facilitates troubleshooting, as the history of changes made to systems and software is readily available, enabling faster root cause analysis and resolution.
- Risk reduction: Configuration management reduces the risk associated with changes, configuration drift, and inconsistencies in systems. By enforcing proper configuration control procedures and maintaining accurate documentation, organizations can minimize the chance of errors or security vulnerabilities creeping into their infrastructure.
- Compliance and audit readiness: Configuration management supports compliance efforts by providing a clear record of system configurations. It enables organizations to demonstrate adherence to regulatory requirements and industry standards during audits, ensuring transparency and accountability.
- Improved Asset Management: The Configuration Management process uses the CMDB to keep track of all assets that have been deployed. This information is valuable for both the Software Asset Management (SAM) and Hardware Asset Management (HAM) processes, as it assists in maintaining license compliance and controlling hardware expenses.
Configuration Management and Cyber Security
Configuration Management is a critical component of cybersecurity that focuses on maintaining a detailed inventory of an organization's IT assets and configurations.
By adopting robust Configuration Management practices, organizations can ensure the secure configuration of all hardware and software components according to standardized and hardened images.
Utilizing hardened images helps maintain consistency and compliance across the IT environment, protecting critical assets from vulnerabilities and ensuring a strong cybersecurity posture.
This proactive approach allows for rapid identification of unauthorized changes or vulnerabilities in the IT environment, enabling timely remediation before security incidents occur.
Moreover, robust configuration management enhances compliance with industry regulations by providing a clear audit trail of configuration changes and consistent application of security policies across the entire IT infrastructure.
Implementing these best practices in Configuration Management is essential for safeguarding against potential security breaches and ensuring the integrity of IT systems.
Read our post on Boosting Cyber Resilience with IT Security Assessments and ITSM Processes for more information on improving your cyber security posture.
Configuration Management Roles and Responsibilities
Having clearly defined roles and responsibilities is crucial for the efficient execution of any process. This clarity helps ensure that everyone is on the same page and clearly understands their place in the process.
Process roles are not to be confused with any hierarchical status within the organization, and their responsibilities are limited to that particular process.
Here are some typical Configuration Management roles:
Configuration Management Process Owner
A Senior Manager who is responsible for ensuring that all departments within the IT organization implement and use the process effectively.
Their specific tasks include:
- Defining the process's mission.
- Communicating process goals and objectives to all stakeholders.
- Resolving any cross-functional issues.
- Ensuring consistent execution across departments.
- Reporting on process effectiveness to senior management.
- Initiating process improvements as necessary.
Configuration Manager
The Configuration Manager is responsible for the day-to-day execution of the process. They take direction from the Process Owner in order to ensure consistent execution of the process across all areas of the organization. Larger organizations may have multiple people in this role.
Specific responsibilities include:
- Managing the day to day activities of the process
- Gathering and reporting on process metrics
- Tracking compliance to the process
- Escalating any issues with the process
- Acting as chairperson for process meetings
- Governance of the Configiration Management System (CMS) comprised of one or more Configuration Management Databases (CMDB)
Configuration Management Analyst
The Configuration Management Anslyst is responsible for maintaining the accuracy of the data in the CMDB. In larger organization these responsibilities are distributed across multiple Configuration Managememt Analusts.
Specific responsibilities include:
- Record and maintain CIs within the CMDB
- Validate accuracy of CMDB data and report discrepancies
- Ensure all changes to configuration items are authorized
- Assist in executing configuration audits
- Scheduling and creation of status accounting reports
Configuration Item (CI) Owner
This role entails managing a particular category of one or more Configuration Items. The CI Owner is the definitive source of information for all attributes pertaining to that CI class.
Configuration Management Activities
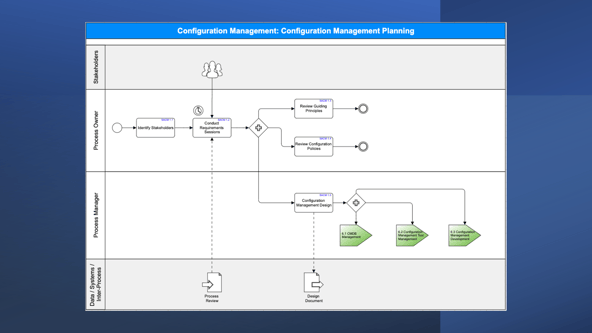
Here at Navvia, we strongly believe in simplifying complex processes by breaking them into high-level activities.
These activities serve as a guide, outlining the crucial steps in the process and the connections between them. We then map out the detailed tasks required to complete each activity. Organizing processes in this way makes understanding and communicating the process easier.
The following are the critical activities of the Configuration Management Process.
Configuration Management Planning
The purpose of the Configuration Management Planning activity is to ensure that Configuration Management aligns with the requirements and abilities of the company and its ITSM processes.
The team responsible for configuration management, along with important decision-makers, determine the appropriate level of configuration management needed to effectively support the services provided by the organization.
They establish a plan for achieving this level and document it in a configuration management plan.
Although this task is typically done only once during the initial implementation of the process, it's considered best practice to regularly review the plan to ensure that it's still meeting the organization's support needs. This falls under the Development Maintenance activity related to Continuous Service Improvement.
Configuration Item (CI) Identification
This activity involves the necessary steps to plan and prepare for the identification of Configuration Items (CIs).
This includes creating a model of the infrastructure to determine the appearance and relationships of CIs.
Additionally, it entails establishing naming conventions, enterprise taxonomy, and selecting and identifying software and document libraries.
This Activity also involves setting up the Configuration Management Database (CMDB) and updating it with new types, classes, and attributes of CIs.
Configuration Control
The Configuration Control activity oversees any updates made to the CMDB and CMS.
In the case of Managed CIs, Configuration Control ensures that any changes made are approved through a Change Request.
For both Unmanaged and Managed CIs, Configuration Control ensures that all information stored in the CMDB or CMS is accurate and complete.
Any unauthorized changes will be sent to Change Management for further instructions, while any discrepancies or errors in the CI configuration will be forwarded to the CI Owner for resolution.
Verification and Audit
The process of Verification and Audit involves reviewing and verifying the physical existence of Configuration Items (CIs) to ensure accurate representation in the Configuration Management Database (CMDB).
If discrepancies are found, Change Management is consulted to determine the appropriate corrective action, which may involve updating the CMDB or modifying the CI to match the CMDB.
Verification Audit does not involve updating the CMDB, as this is the responsibility of Control Activity. Any changes made to the CMDB to resolve discrepancies must be approved through a Change Request (CR) to maintain a complete audit trail.
The responsibility of updating a CI lies with its owner, but must also be approved by Change Management.
Status Accounting and Reporting
Status Accounting falls under the reporting activity of Configuration Management. Its primary purpose is to generate both regular and ad-hoc reports on the current, past and future status of the infrastructure and the CIs that Configuration Management oversees.
Maintenance and Continuous Service Improvement
This activity's purpose is to develop and maintain the configuration management system and all of its components.
As part of the configuration management planning activities, the requirements are collected and then passed on to the tasks in this activity for further processing.
Improving all components, such as the CMDB, configuration management tools, scripts, and other necessary items to support the process, is a crucial aspect of this activity.
This activity will require regular housekeeping and maintenance of the developed components and scripts.
Continuous Service Improvement involves regularly measuring and monitoring process efficiency and effectiveness. Ongoing activities are undertaken to identify, plan, and implement improvements.
Configuration Management Process Governance
Process governance is an essential aspect of the Configuration Management process. It involves establishing a framework to ensure an organization effectively manages and executes the process.
The Configuration Management process owner plays a critical role in process governance, defining the process's mission and communicating its goals and objectives to all stakeholders. They also resolve cross-functional issues and initiate improvements to enhance the process's effectiveness.
The Configuration Manager oversees the daily implementation of the process, ensuring uniform execution throughout the organization. They collect and present process metrics, monitor compliance and report process-related issues.
Working as a team, the process owner, process manager, and other stakeholders should periodically assess the process looking for gaps and potential areas of improvement. One way to do this is through a formal process assessment. Learm more about assessments by reading The Importance of a Process Maturity Assessment.
Through process governance, organizations can maintain consistency, efficiency, and continuous improvement in their Configuration Management practices.
Configuration Management Process Design and Implementation
Believe it or not, implementing an ITSM process is more complex than just installing an ITSM tool. It requires a well-defined process to ensure a successful implementation. To help organizations navigate this process, we recommend following these five steps:
- Identify gaps in your current process and supporting tools: Before implementing a new process, it's important to assess your existing process and tools to identify any areas that may need improvement. This review should include outdated documentation, gaps in ITSM tool functionality, or lack of integration between different systems.
- Collaborate with stakeholders to understand their process requirements: Involving all relevant stakeholders in the implementation process is crucial. These stakeholders include not only the information technology team but also all business stakeholders. By engaging with stakeholders early on, you can gather their input and ensure that their requirements are included in the design and implementation of the Configuration Management process.
- Define and document your Configuration Management process: Once you have identified the gaps and gathered input from stakeholders, it's time to define and document your Configuration Management process. This task involves clearly defining the steps and activities involved in managing changes, as well as establishing roles and responsibilities. It's important to align the process with industry best practices, such as ITIL (Information Technology Infrastructure Library), COBIT, or ISO20000 to ensure consistency and efficiency.
- Capture user stories and requirements to guide the developer or implementer: To effectively implement the Configuration Management process in the ITSM tool, capturing user stories and requirements is crucial. This activity involves understanding end-users specific needs and expectations and translating them into actionable tasks for the developer or implementer, ensuring the tool meets user needs.
- Ensure sustainability by providing ITSM training, defining controls, reporting metrics, and implementing governance: To ensure long-term success, provide Configuration Management training to users and Information Technology organization staff. In addition, define controls for process governance, track performance with metrics, and implement continuous monitoring and improvement.
By following these five steps, organizations can ensure a successful implementation of the Configuration Management Process and supporting ITSM tools.
Additional Resources
Here are links to additional resources to
- Webinar: Leading a Successful ITSM Tool Implementation
- Webinar: Best Practices in Process Design and Documentation
- Blog: An Introduction to Process Mapping
- Blog: Process Documentation: A Complete Guide
- Blog: Building the Business Case for ITSM Brest Practices
Configuration Management is an integral component of your foundational ITSM processes and cannot be overlooked. It provides crucial information necessary for the efficient handling of Incident, Problem, Change, and Release Management.